Updated 29 April 2025 at 16:34 IST
Pahalgam Aftermath: Desperate In Diplomacy, Defeated In Cyberspace; Pakistan’s Cowardly Cyberattacks Flop
In late April 2025, Indian cyber agencies foiled multiple hacking attempts by Pakistan-based actors targeting publicly accessible defence-affiliated websites.
- Defence News
- 6 min read
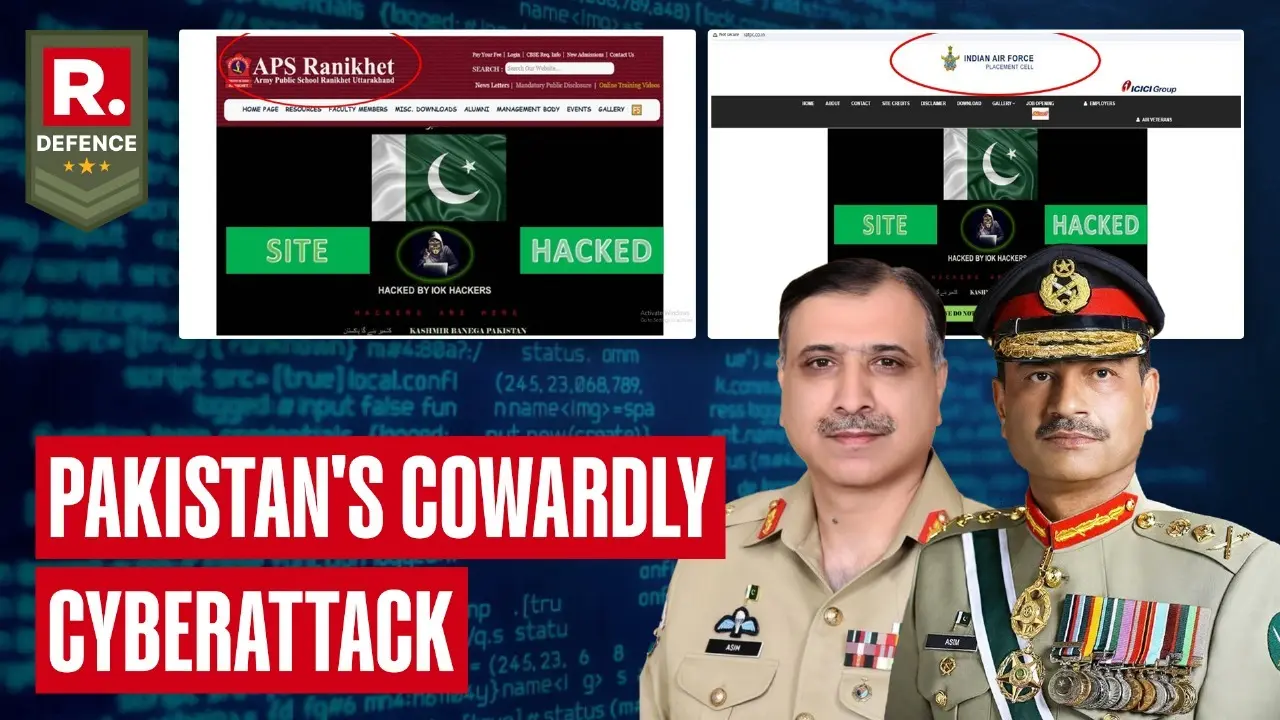
New Delhi, India - In the wake of the April 22 Pahalgam terror attack and renewed ceasefire violations along the Line of Control, Islamabad appears to have shifted to online provocations. In late April 2025, Indian cyber security agencies detected and blocked several coordinated attacks on publicly accessible military-related websites.
Intelligence assessments confirm that four sites – all related to the Indian Army or Air Force – were targeted by Pakistan-based hackers operating under the pseudonym “IOK Hacker” (Internet of Khilafah) . These intrusions were promptly isolated and neutralized in real-time by India’s layered cyber defences, and no operational or classified networks were compromised at any stage. Officials emphasized that the attempts, though disruptive, ultimately failed and underscored the attackers’ limitations.
- Army Public School, Srinagar: Hackers defaced the school’s website with anti-India propaganda and launched a DDoS (distributed denial-of-service) assault. The website was isolated and restored without affecting any internal Army networks .
- Army Public School, Ranikhet: Its site was similarly defaced with inflammatory content; the attack was detected and reversed before any damage occurred.
- Army Welfare Housing Organisation (AWHO) portal: An intrusion attempt on AWHO’s member database was detected and blocked immediately; no soldier or family data was exposed.
- Air Force Placement Organisation: Indian defenders also foiled an effort to compromise this portal (used for personnel placement); that site too was isolated and secured.
Pak Targets Indian Defence Sites, Forgets India Doesn’t Run on Propaganda Servers
All four intrusions were traced back to Pakistani servers, according to official reports. Indian Army sources note that operators calling themselves “IOK Hackers” sought to “deface pages, disrupt online services and harvest personal information”.

In each case, India’s multi-layered cybersecurity architecture – including military CERT systems and network segmentation – detected the anomaly in real-time and cut off the threat. “These frustrated attempts highlight both the adversary’s intent and its limitations,” the Army said, adding that its cyber posture is continually upgraded to safeguard soldiers and their families.
Advertisement
Aftermath of the Pahalgam Attack: A Frustrated Escalation to Cyber Warfare
Indian officials explicitly link these cyber assaults to the tense atmosphere following the Pahalgam massacre. “Pakistan-based cyber actors have once again failed in their attempts to violate Indian cyber sovereignty,” a defence official told the press. The statement noted that, after being unable to penetrate critical military networks, “Pakistan has redirected its efforts towards publicly accessible welfare and educational websites”. In other words, Islamabad’s cyber campaign is seen as a retaliatory cyber-escalation in response to the Pahalgam incident. Analysts describe this pivot to hacking schools and welfare sites as a “cowardly” form of warfare: low-risk propaganda operations that avoid direct military confrontation.

This development parallels ongoing kinetic exchanges. Security agencies report that, in the same period, Pakistani forces carried out repeated small arms firing across the LoC (five days in a row), prompting swift Indian retaliation. With conventional surprises thwarted by Indian vigilance, the “Internet of Khilafah” hackers appear to have settled for digital skirmishes. Their strategy – disseminating propaganda via Army school websites and probing support systems – underscores rising frustration in Islamabad. However, Indian statements emphasize that these are “publicly accessible” (non-core) sites, chosen only after the most sensitive networks proved impenetrable.
Advertisement
Historical Context: Pakistan-Linked Cyber Threats Against India
India has long faced cyber threats attributed to Pakistan’s intelligence services. Groups such as Transparent Tribe (APT36) have routinely targeted the Indian military, government and educational sectors in recent years. For example, a 2024 report by cybersecurity firm BlackBerry found that between late 2023 and April 2024, a Pakistan-based group (believed to be Transparent Tribe) launched espionage campaigns against Indian defence and aerospace organisations. Security firm Seqrite (the enterprise arm of Quick Heal) similarly documented that Transparent Tribe “originated in Pakistan” and “has been targeting Indian government and military entities” for the last decade. Notably, since 2022 this group expanded into higher education, infiltrating Indian Institutes of Technology and other institutions as well. More recently, the SideCopy cluster (an offshoot of APT36) was caught using sophisticated malware to target defence research facilities.

Despite these persistent campaigns, most Pakistani-linked hacks against India have been detected early or partially mitigated. The recent spate of defacements fits this pattern: flashy but ultimately superficial. Even incidents like the 2024 Burger Singh fast-food website hack (claimed by a Pakistani group in protest of a promo code) caused only temporary disruption. Cybersecurity experts note that many Pakistan-aligned attackers rely on phishing lures and propaganda stunts rather than deep infiltration. In the latest case, Indian analysts quickly traced the actors back to Pakistan and confirmed no critical systems were breached. “The adversary’s intent” – to embarrass or alarm through defacement – “and its limitations” – inability to access core networks – were both made clear, an Army statement said.
Implications for India’s Security and Defense Posture
While the thwarted hacks caused no loss of classified information, they carry important lessons for India’s national security. First, the targeting of schools and welfare portals underscores the attackers’ intent to undermine morale and spread propaganda among military families. Protecting such non-classified but sensitive systems (housing records, educational sites, etc.) is now recognized as part of military cyber-defence. India’s response – swift isolation of affected servers and “restorative action” within hours – reflects a maturing digital defence framework.
Second, the incidents reinforce the value of a multi-layered cybersecurity architecture. As noted by Indian officials, real-time monitoring and redundancy prevented any spillover into secure networks. The Defence Cyber Agency (created in 2019) and other agencies have been beefing up network segmentation, intrusion detection and incident response across the armed forces. These tools – combined with regular cyber exercises and intelligence sharing – are credited with “continually upgrading India’s cyber posture”.
In sum, New Delhi’s cyberspace has emerged unscathed from this round of Pakistani forays. Multiple official statements highlight that “no operational or classified networks were affected” . Still, the episode underlines that national security no longer stops at the barracks gates – it extends into code and servers. Indian cyber defenders remain on alert, treating even “cowardly” low-level attacks as potential preludes to something worse. By publicly revealing the thwarted hacks and tracing them to Pakistan, New Delhi also sends a message: it will expose and counter every facet of external aggression, whether on the ground or online.
Watch- Pakistan Launches 'Dirty' Digital Strike, India Foils Attack Attempts | Pahalgam Terror Attack
Published By : Yuvraj Tyagi
Published On: 29 April 2025 at 16:34 IST
